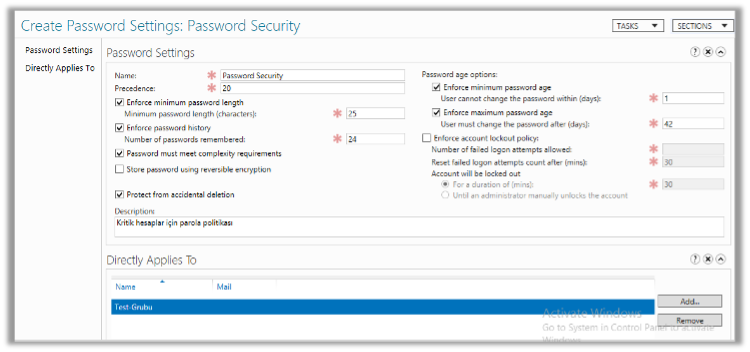
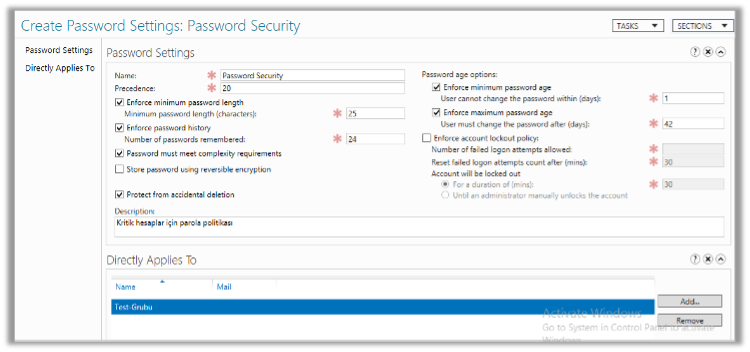
The security of critical accounts (such as service accounts) in organizations is important. It is recommended to gather these accounts under a security group and apply a specially created password policy for this group.
The recommended settings are as follows. After configuring the settings, simply add the group in the Directly Applies To section.
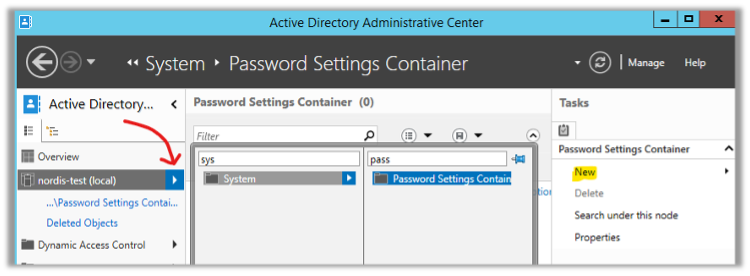
If you want to implement this policy for all users at the domain level, you can create a new GPO and assign it to users.
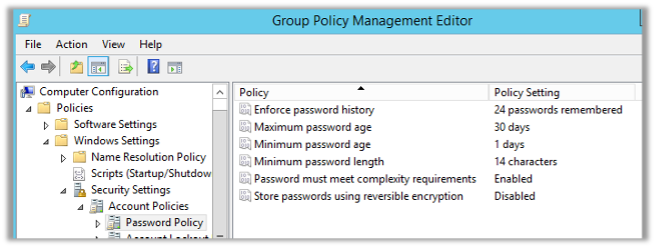
Note: In a policy prepared through GPO, the minimum character count cannot exceed 14. If you want it to be more than 14 characters, this change needs to be made through the Administrative Center as in the first example.
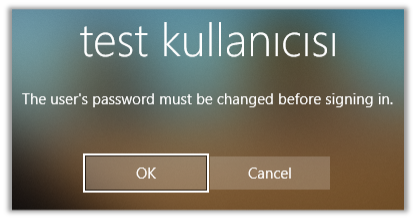
If you want to force users to change their passwords at their next login after applying this GPO, you can deploy it to the selected OU using the following command.
Get-ADUser -Filter * -SearchBase “OU=OU NAME,DC=DOMAIN,DC=COM/LOCAL” | Set-ADUser -CannotChangePassword:$false -PasswordNeverExpires:$false -ChangePasswordAtLogon:$true
When you enter this command, the “User must change password at next logon” checkbox will be checked for users who are members of the specified OU, and they will need to change their passwords at their next login attempt.
Service account passwords (such as SQL Agent) are typically not changed after installation. This can be checked using the following PowerShell command:
net user <service account name> /do
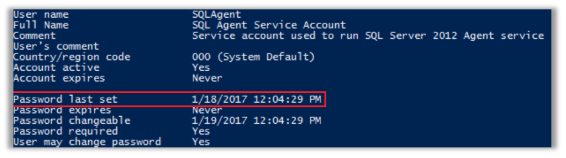
Service account passwords that haven’t been changed for a long time can be cracked by an attacker. It is recommended to change these service account passwords every 6 months or annually.