The SMB Protocol uses data encryption for all Windows operating systems for file sharing, printer sharing, and Windows management to prevent the modification of transmitted packets. This feature must be enabled on both the server and client sides. This ensures that client computers without SMB signing enabled cannot communicate with the server.
***Enabling SMB packet signing reduces the performance of file service operations by 15%.
Relevant registry setting:
HKLM\System\CurrentControlSet\Services\LanManServer\Parameters\RequireSecuritySignature
It is possible to protect against this vulnerability by enabling the setting Microsoft network server: Digitally sign communications (always).
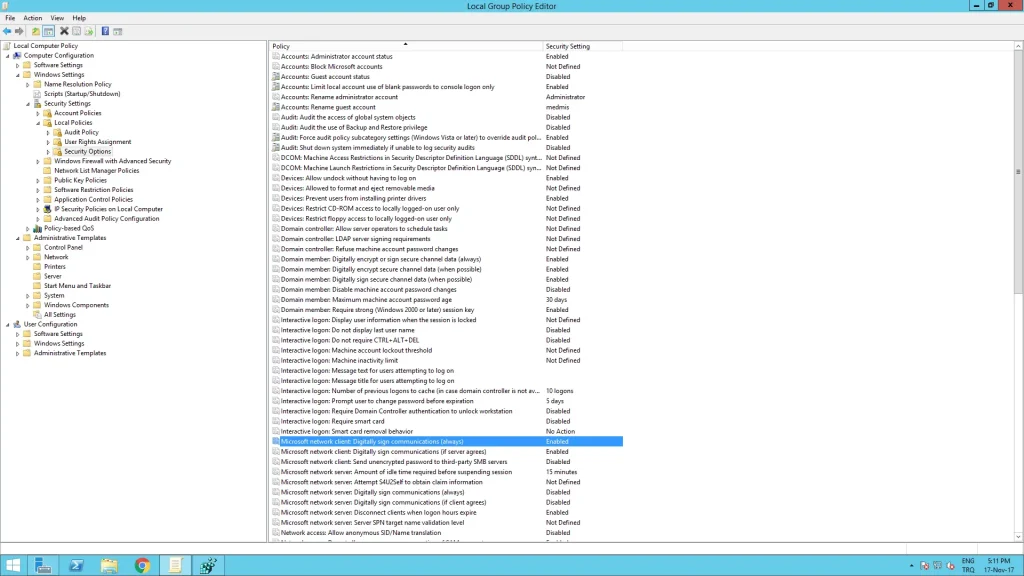
If you are doing this on a local computer
start>run>In Gpedit, under security local security
Microsoft network client: Digitally sign communications (always) is enabled
If you are doing this with GPO, you can follow the same steps; you can create a group policy instead of gpedit.
Additionally, after testing, you can also change the settings of the following policies.
Computer Configuration->Policies->Windows Settings->Security Settings->Local Policies->Security Options
Disable Microsoft Network Client: Digitally Sign Communications (Always).
Disable Microsoft Network Server: Digitally Sign Communications (Always).
Enable Microsoft Network Client: Digitally Sign Communications (If Server Agrees).
Enable Microsoft Network Server: Digitally Sign Communications (If Client Agrees).
If these settings are not enabled for signing on your client and server, you may not be able to access shared folders, so we recommend that you do not try them on real systems without testing.